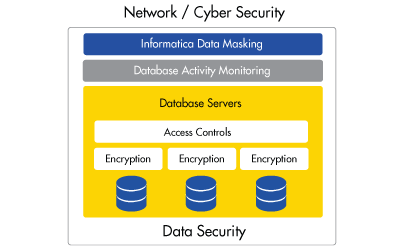
Informatica Data Masking
 Nbiz Infosol as an authorized distributor for Informatica - Data Masking Solutions which prevents unauthorized users from accessing sensitive information with real-time data de-identification and de-sensitization.
Nbiz Infosol as an authorized distributor for Informatica - Data Masking Solutions which prevents unauthorized users from accessing sensitive information with real-time data de-identification and de-sensitization.
Your IT organization can apply sophisticated masking to limit sensitive data access with flexible data masking rules based on a user’s authentication level. Blocking, auditing, and alerting your users, IT personnel, and outsourced teams who access sensitive information, it ensures compliance with your security policies and industry and civil privacy regulations.
Dynamic Data Masking also lets you:
- Dramatically decrease the risk of a data breach
- Easily customize data-masking solutions for different regulatory or business requirements
- Protect personal and sensitive information while supporting offshoring, outsourcing, and cloud-based initiatives
- Secure big data by dynamically masking sensitive data in Hadoop.
For more details Click Here
Protect live data with dynamic data masking and data for outsourcing, test, and customer support with persistent data masking.
- Precision for data privacy laws
Automate the identification of sensitive data locations for consistent masking within and across databases.
- Powerful masking capabilities
Pre-defined, customizable library of masking functions for sensitive data elements including PII, PHI, and PCI.
- Performance
Provide scalable data masking capabilities for heterogeneous applications.
- Role-based masking
Protect sensitive data in applications based on user role, location, and time of access.
- Data connectivity
Relate a wide range of distributed and mainframe data sources for enterprise data privacy and security.
- Monitoring and compliance reporting
Engage compliance, risk, and audit teams to ensure ongoing alignment with data governance initiatives.
 Ponemon Institute Research: How IT security is addressing threats to structured and unstructured data
Ponemon Institute Research: How IT security is addressing threats to structured and unstructured data
What scares IT security more than hackers?
We commissioned the Ponemon Institute to answer that question and then some. In a survey of more than 1,500 IT practitioners from around the world, they reveal what’s worrying the people tasked with protecting the enterprise’s most sensitive data.
With the rise of the data-centric enterprise, there is a necessary and parallel development of the security architecture meant to protect it. But in the time it’s taken for data security to catch up with the changing datascape, organizations have found their compliance and data protection programs vulnerable.
Whitepaper and case study:
 01779 dynamic-data-masking ds en-US.pdf
01779 dynamic-data-masking ds en-US.pdf



 Special Offers
Special Offers
 GET OUR BEST DEALS!
GET OUR BEST DEALS!